Our Blog

The AI Vendor Interrogation
The sales demos look incredible. The promises are world-changing. But if you don’t know how to look under the hood, your next AI investment could become your biggest liability. The Incredible Shrinking Margin Between Hype and Reality If you are a founder or CEO…
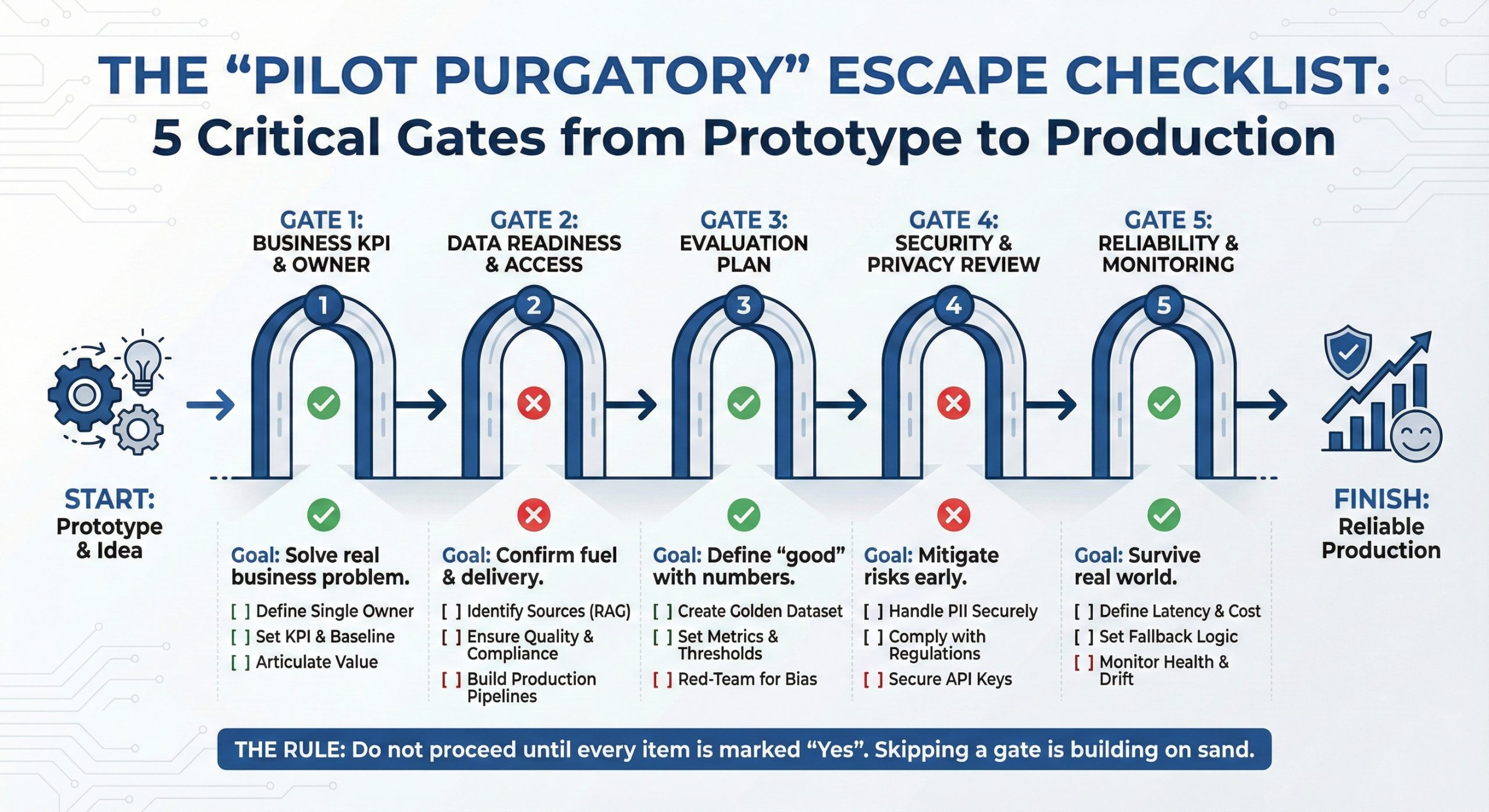
The “Pilot Purgatory” Escape Checklist
The 5 Critical Gates from Prototype to Production Overview This checklist is designed to help founders and leadership teams prevent AI projects from stalling in “Pilot Purgatory.” Use it to evaluate your initiative at each stage. The Rule: Do not proceed to the next…

Enhancing Engineering Teams Through Fractional CTO Leadership And Guidance
Understanding The Role Of A Fractional CTO In Engineering Leadership With technology evolving so quickly, engineering teams must stay flexible and keep up with new trends. A fractional Chief Technology Officer (CTO) offers expert leadership without the need for a…

Unlocking Cybersecurity: The Essential Guide For Every Beginner
Understanding The Basics Of Cybersecurity: Encryption, Malware, And Internet Security Understanding the basics of cybersecurity is crucial for anyone navigating the digital world. At the heart of cybersecurity lies encryption, a process that transforms information…

Data Breaches: How to Protect Your Company’s Sensitive Information
Strengthening Employee Training To Combat Phishing Attacks In the realm of safeguarding sensitive company information, strengthening employee training to combat phishing attacks is paramount. Phishing remains one of the most effective tactics employed by…

Don’t Take the Bait! Learn How to Spot and Sidestep Phishing Traps
Understanding The Basics: What Are Phishing Scams And How Do They Work? Phishing scams are deceitful attempts by malicious actors to obtain sensitive information such as usernames, passwords, and credit card details by masquerading as a trustworthy entity in…

The Future of Cybersecurity Training: Emerging Trends
The Evolution Of Cybersecurity Training: Adapting To An Ever-Changing Landscape The evolution of cybersecurity training has been a dynamic journey, adjusting continuously to keep pace with the ever-changing landscape of digital threats. In its early days,…
Top 5 Mistakes To Avoid In Your Cybersecurity Training Program
Overlooking The Importance Of Regular Updates In Employee Education In the rapidly evolving landscape of cybersecurity, overlooking the importance of regular updates in employee education can severely compromise an organization’s defenses. Cyber threats are…

The Essential Cybersecurity Skills Every Employee Needs
Understanding Security Policy: The Foundation Of Workplace Cybersecurity Understanding security policy is fundamental to establishing a robust cybersecurity framework within an organization. At its core, a security policy serves as a comprehensive guide, delineating…

Fortifying Your Defenses: Practical Tips To Prevent Social Engineering Attacks
Understanding Social Engineering: The Role Of Psychological Manipulation In Cybersecurity Breaches Social engineering is a form of manipulation that exploits human psychology to breach cybersecurity measures. Unlike traditional hacking, which targets…